Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

In my years as a network consultant and ISP, I’ve seen firsthand how DDoS attacks can cripple even the most robust networks. Imagine this: your network is like a busy highway, but suddenly, someone jams every lane with thousands of fake vehicles, preventing real cars from moving. That’s essentially what happens during a DDoS attack. Whether you’re running a small ISP or managing a large network, DDoS attacks can bring everything to a halt. But with the right strategies in place, you can keep traffic flowing smoothly even during an attack.
Your MikroTik router is like a gatekeeper for your ISP’s network. Normally, it efficiently lets in legitimate users while keeping out the troublemakers. But during a DDoS attack, the gatekeeper is overwhelmed by fake requests, making it impossible to differentiate between friends and foes. This results in legitimate traffic being blocked and your services grinding to a halt.
In my years as a network consultant and ISP, I’ve seen firsthand how DDoS attacks can cripple even the most robust networks. Imagine this: your network is like a busy highway, but suddenly, someone jams every lane with thousands of fake vehicles, preventing real cars from moving. That’s essentially what happens during a DDoS attack. Whether you’re running a small ISP or managing a large network, DDoS attacks can bring everything to a halt. But with the right strategies in place, you can keep traffic flowing smoothly even during an attack.
During one particularly stressful morning, I watched our network traffic spike, thinking it was an increase in customer demand. But in reality, we were under a coordinated DDoS attack. It felt like a flood of illegitimate requests were jamming our servers, much like a sudden downpour overwhelming a drainage system.
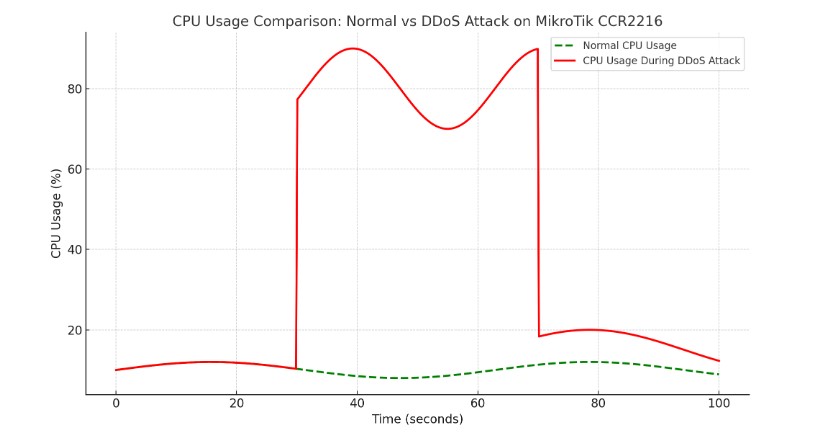
This graph effectively illustrates the strain placed on the router’s resources when under attack compared to normal operations.
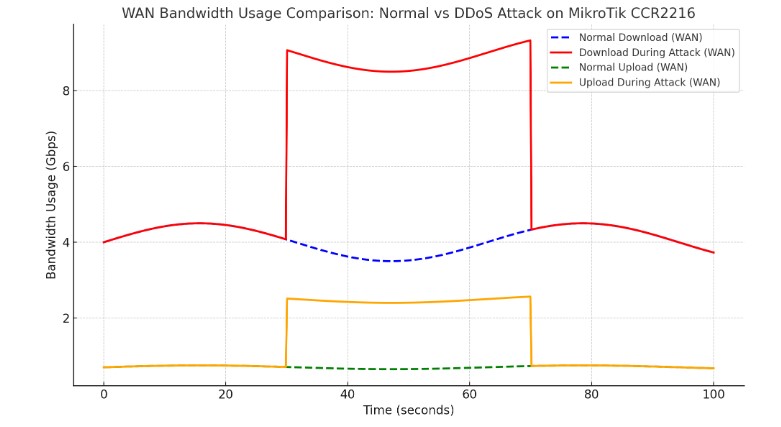
Here’s the graph comparing WAN bandwidth usage (download and upload) on a MikroTik CCR2216 during normal conditions versus a DDoS attack.
This visual highlights how bandwidth surges dramatically during an attack, impacting the WAN interface.
I’ve since implemented a few best practices to protect our network, and they’ve proven highly effective. Here’s how I protect ISP networks with MikroTik routers.
Imagine managing a dam—you need sensors to alert you when too much water is coming in. For DDoS protection, your MikroTik router needs similar sensors to detect unusual traffic spikes. One of the most effective detection methods is the dst-limit feature, which monitors traffic flow based on IP addresses. Here’s a simple configuration to detect abnormal spikes:
/ip firewall filter add chain=forward connection-state=new action=jump jump-target=detect-ddosThis line redirects all new connections to a dedicated detection chain, detect-ddos. Next, we apply a dst-limit rule to monitor traffic. Think of it like setting a threshold on how much water (traffic) should flow in.
/ip firewall filter add chain=detect-ddos dst-limit=32,32,src-and-dst-addresses/10s action=returnIn this example, the rule monitors for up to 32 packets within 10 seconds from the same source-destination combination. If traffic exceeds this limit, we know an attack is underway.
Once the attack is detected, you need to act quickly. It’s like opening a floodgate to divert excess water. In networking terms, this is done by adding the attackers and targets to address lists. Once identified, we drop any further traffic between them.
/ip firewall address-list add list=ddos-attackers
/ip firewall address-list add list=ddos-targets
/ip firewall raw add action=drop chain=prerouting dst-address-list=ddos-targets src-address-list=ddos-attackersThis configuration adds malicious IPs to the ddos-attackers list and the victims to the ddos-targets list. Then, any communication between attackers and targets is dropped by the firewall to ensure legitimate traffic can pass through unaffected.
SYN flood attacks are like someone knocking on your door continuously but never actually entering. They consume all your time and attention, leaving legitimate visitors waiting outside. To stop this, MikroTik has a feature called tcp-syncookies. It helps by allowing only genuine connection requests while filtering out the noise.
/ip settings set tcp-syncookies=yesThis feature ensures that only real connections complete the SYN-ACK handshake, preventing your server from being overwhelmed by fake SYN requests.
SYN-ACK floods take the attack a step further, bombarding your router with spoofed SYN-ACK packets. It’s like someone spamming you with responses to questions you never asked, overwhelming your ability to process legitimate requests. To counter this, we can use a similar dst-limit rule but apply it to specific TCP packets with the SYN-ACK flag.
/ip firewall filter add action=return chain=detect-ddos dst-limit=32,32,src-and-dst-addresses/10s protocol=tcp tcp-flags=syn,ackBy limiting the rate of SYN-ACK packets, you effectively reduce the load on your router and prevent service disruption.
As an ISP, our challenges are more complex. Unlike single-network operations, we are responsible for managing traffic for thousands of users. A DDoS attack doesn’t just affect our services—it impacts every customer who relies on our network.
From my experience, here’s how you can fine-tune these firewall rules specifically for ISP networks:
dst-limit thresholds based on your network’s typical usage.Pro Tips for Protecting MikroTik Routers from DDoS Attacks:
Always enable TCP SYN cookies to protect against SYN flood attacks, allowing your router to handle connection requests more efficiently. Utilize address lists to categorize and filter known malicious IPs, ensuring that only legitimate traffic is allowed through. Additionally, regularly monitor your network traffic patterns to quickly identify any unusual spikes, enabling you to respond promptly to potential DDoS attacks.
Protecting your MikroTik router from DDoS attacks is essential for maintaining the integrity and performance of your ISP services. By implementing strategies such as enabling TCP SYN cookies, utilizing address lists, and monitoring traffic patterns, you can significantly enhance your network’s resilience against potential threats. Remember that a multi-layered approach, combining internal measures with external DDoS protection services, is key to effectively safeguarding your infrastructure. Regularly updating your devices and minimizing unnecessary services further reduces vulnerabilities, ensuring your network remains robust against ever-evolving attack vectors. By staying proactive and informed, you can help secure your MikroTik routers and provide uninterrupted service to your customers.